India IT Act of 2000 (Information Technology Act)
India's Information Technology Act, 2000 (IT Act) is a subject of contention and controversy. As it is amended, it contains some of the most stringent privacy requirements in the world and has the unfortunate impact of holding intermediaries liable for illegal content.
You can read the contents of the act here.
If you operate from India, you need to understand the IT Act in order to avoid potential penalties.
This article will give an overview of the act, discuss the provisions and requirements set forth in the IT Act and provide a compliance checklist so your privacy and data protection strategies are planned correctly with the context of this law.
Provisions of the IT Act 2000
The IT Act of 2000 passed in a budget session of parliament and signed by President K.R. Narayanan in 2000. It underwent further finalization by India's Minister of Information Technology, Pramod Mahajan.
The original act addressed electronic documents, e-signatures, and authentication of those records. It also enacted penalties for security breach offenses including damaging computer systems or committing cyber terrorism. Regulating authorities received power to monitor these situations and draft rules as situations arose.
The IT Act underwent changes as Internet technology grew. In 2008, additions expanded the definition of "communication device" to include mobile devices and placed owners of given IP addresses responsible for distributed and accessed content.
Privacy was addressed in 2011 when stringent requirements for collecting personal information came into effect.
The most controversial change in this act involved section 66A. It make "offensive messages" illegal and holds the owners of servers responsible for the content, and has since been struck down.
Penalties range from imprisonment of three years to life and fines. Offenses that occur in a corporate setting can result in further administrative penalties and bureaucratic monitoring that can prove burdensome to doing business.
Requirements of IT Act 2000
The IT Act 2000 applies to companies that do business in India. This includes entities registered in India, ones that outsource there, and ones that maintain servers within the country's borders.
The act covers all activity involving online exchanges and electronic documents.
If your only connection with India is having customers there, you are not held to the IT Act. The only way that can occur is if you run a service or sell a product and also maintain servers there.
For example, Instagram is popular in India with many people participating in that social media app. However, Instagram is a U.S. company and does not need policies complying with the IT Act.
However, Snapdeal, an online shopping source in India, is an Indian company that conducts transactions in India. It is held to the stipulations in the IT Act 2 - and that is addressed in its Privacy Policy page:

Compliance Checklist for IT Act 2000
Complying with the IT Act and the privacy requirements that follow requires some effort.
In the end, you will have a more secure system that consumers can use in confidence. These steps will help you meet the requirements of the law in the most efficient way possible.
Know the location of your servers
India's IT Act can be a difficult law to follow. It is also one of the few Internet protection and privacy laws that puts responsibility for content on intermediaries, meaning the companies that own the server.
If your company is located in India and registered there, there is no doubt that you must comply with the act. The same is true if your company is a foreign entity that outsourced to India or maintains servers in India.
Multiple layers of outsourcing can lead to unknown server locations. If you hired a consultant or other company to handle your outsourcing or IT needs, ask them where they keep the servers.
Even if your company is not technically an Indian company, you can still fall under this law if your servers are in India - even if you did not know that was the case.
Follow Privacy by Design
Many offenses listed in this act arise from security breaches.
Look into the Privacy by Design guidelines to not only have a tight Privacy Policy but also the IT security to back it up.
Limit access to your servers and create unique login credentials. Also, develop ways to track use on your servers so if any illegal activity arises, you can link it to an individual rather than make it appear your entire company is culpable.

A good example of this implementation is BillDesk, a payment processing company. Located in Mumbai, its primary service is to assist with bill payments. It maintains many pages on privacy as well as a Privacy Policy page.
It also offers a security explanation to show customers how payments are protected. As you can see, it describes its own Privacy by Design approach in detail with links to relevant sections:

New privacy protection additions passed in 2011 require written permission from users before a company can use personal information. These have been considered burdensome by many companies, although there is also an argument that they provide assurance.
It appears that most companies work in automatic acceptance of privacy rules in their Privacy Policies.

India Times adds a privacy consent in its agreement that is not much different than in other parts of the world:

Snapdeal contains an opt-in and opt-out procedure in its Privacy Policy:
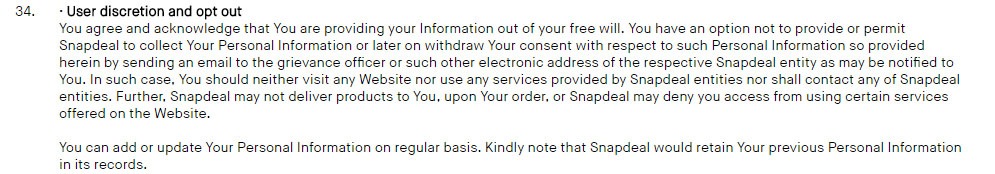
First, make sure your Privacy Policy contains necessary consent and opt out options. Create web links or provide email addresses to facilitate these.
Then, support good Privacy by Design processes so at least your customer's data is secure and you do not face complaints. If you feel better developing written permission processes, take those steps with clickwrap methods perhaps.
Monitor user-generated content
If your online service or app involves exchanging material, develop screening so you can control user-generated content before it posts.
Discovering slanderous content after the fact can still result in legal liability so you want to be as proactive as possible.
Just as avoiding security breaches can keep you in line with privacy and IT protection laws, taking the same approach to possibly illegal content will also help you. You will likely have to implement extensive moderation procedures to control content. Also, your security precautions can prevent hacks and other illegal activity that places disruptive items on your server.
Addressing user-generated content in your Terms and Conditions is also helpful.
BillDesk contains provisions about monitoring client behavior:
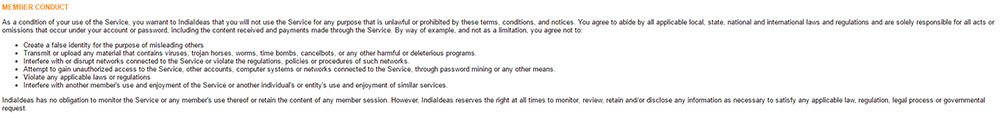
This is important because not only do you need to monitor client use of your servers but you also need the authority to do so.
Placing terms like this in your legal agreements grants that expectation and in some cases, may serve as a deterrent to people who wish to stir up trouble using your systems.
India's IT Act 200 is a stringent yet evolving piece of legislature.
Companies concerned about complying with it would do well to start with Privacy by Design approaches and writing simple language into their Privacy Policy agreements.
Stringent user conduct standards and monitoring use of your systems is also necessary.